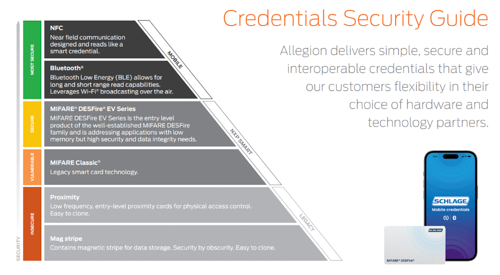
-
Products
 Featured ProductSchlage Credential Services deliver control, security and flexibility without limiting your options. From encryption keys to card tracking and custom artwork, our services help create an access control plan that fits today and grows with you tomorrow.
Featured ProductSchlage Credential Services deliver control, security and flexibility without limiting your options. From encryption keys to card tracking and custom artwork, our services help create an access control plan that fits today and grows with you tomorrow. -
Solutions
-
Resources

- Why Allegion


































.png)