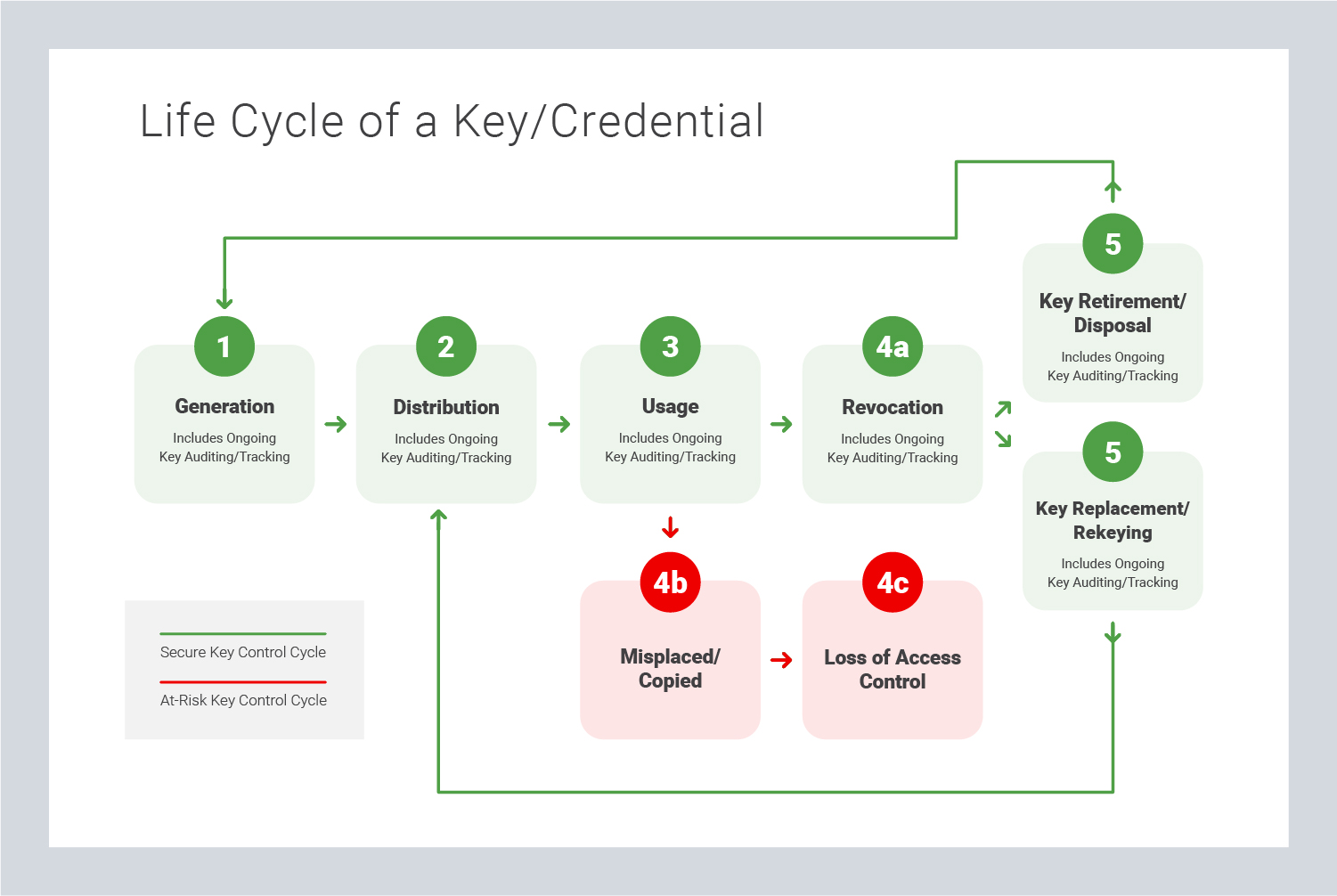
Problem: The Lost Master Key
In a large corporate office building, a security guard loses a master key to the entire premises, including locked offices holding sensitive information, server rooms and mail centers. The missing key was not reported for several days and was duplicated by unauthorized individuals. The company had to re-key all its locks, which was extremely costly and caused significant operational disruptions.
Solution: Lost keys should be immediately reported. Additionally, sensitive keys like master keys should be restricted keys, meaning they can’t be copied.
Problem: The Duplicated Key
In a multifamily apartment complex, a tenant duplicated their keys to give to a friend to check their mail while gone on vacation. The friend was able to access the package and mail room, which posed a threat to other tenants’ mail and sensitive information.
Solution: In addition to tracking the number of keys given to apartment tenants, the keys should be restricted to avoid unauthorized copying.
Problem: The Supply Thief
A school discovered that several keys issued to staff members had been duplicated and used to access restricted storage rooms. The school had an outdated manual system to track key issuance or usage, making it difficult to identify who was responsible. This led to theft of supplies and prompted the school to implement stricter access control.
Solution: Many schools have older, out-of-patent key systems with open keyways for their doors allowing any key holder to have a copy made at a local hardware store. Key control and tracking, along with the use of restricted keys, particularly on perimeter doors, is important in schools, where many people come and go throughout the day.
 Featured ProductSchlage Credential Services deliver control, security and flexibility without limiting your options. From encryption keys to card tracking and custom artwork, our services help create an access control plan that fits today and grows with you tomorrow.
Featured ProductSchlage Credential Services deliver control, security and flexibility without limiting your options. From encryption keys to card tracking and custom artwork, our services help create an access control plan that fits today and grows with you tomorrow.